Emergency DDoS protection
Fill in the form or call +55 (11) 3090-4441.
Submitting this form constitutes free, informed and unambiguous consent for the processing of the personal data provided, under the terms of the General Data Protection Law (LGPD – Law 13.709/2018).
- Try it without any commitment.
- Aggressive SLA. Your problem solved or your money back.
- Zero collateral impact on user experience
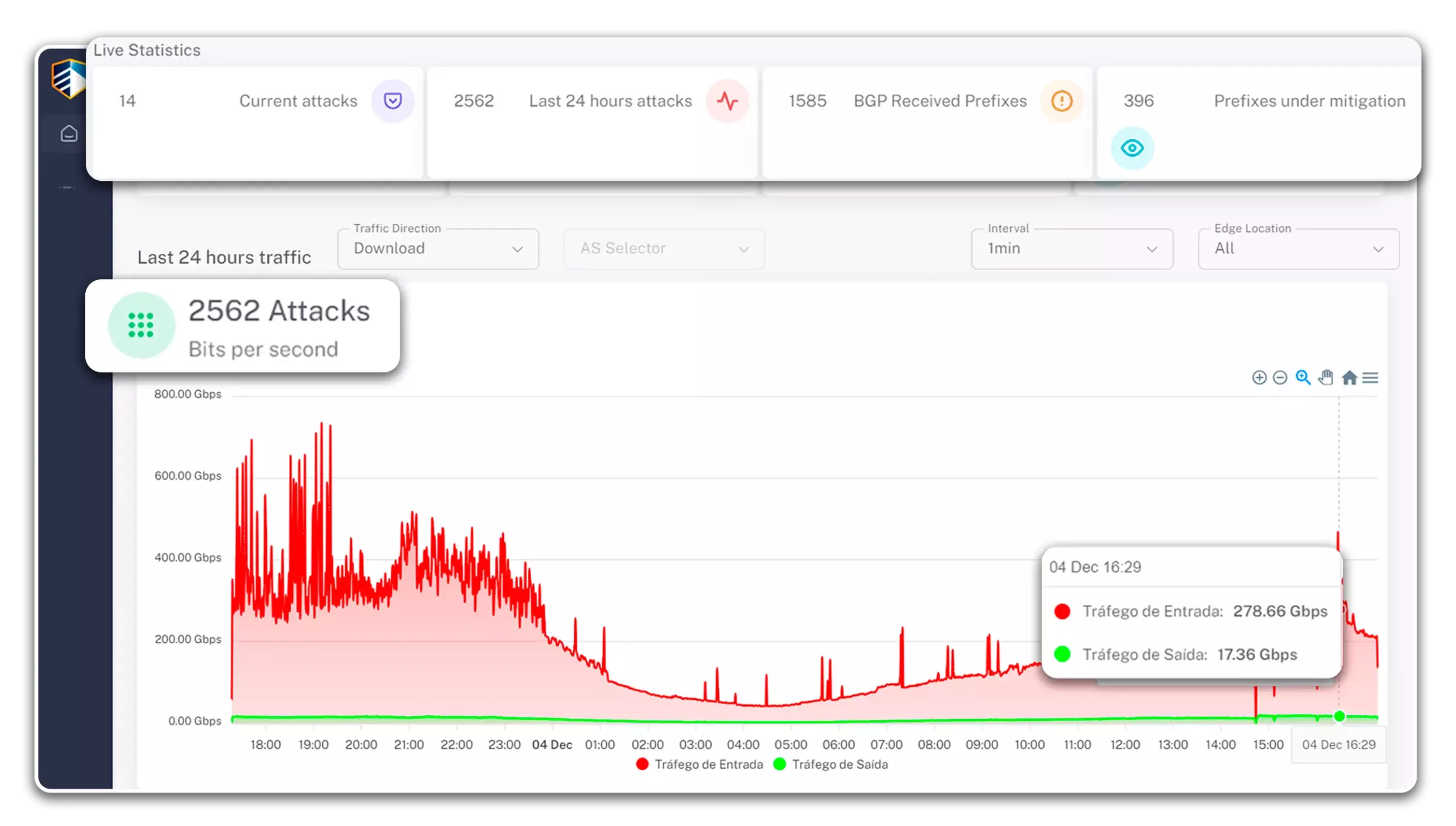
- Track your traffic & insights in real time
- 24x7 direct support with trilingual experts
- Implementation via L3VPN (GRE), or via Layer2 (VLAN/Fiber)
How to connect and protect your operation
Implement our solutions with simple steps, without the need to install additional equipment or licenses.
Cross Connection
A cross connection (or cross connect) in a datacenter is a direct physical connection between different clients within the same facility or datacenter.
GRE Tunnel
Imagine an underground tunnel connecting two distant points. GRE does the same thing, but on the network: it creates a "virtual tunnel" that connects two networks via the Internet, as if they were neighbors.
VLAN in an IXP
In an Internet Exchange (IXP), a bilateral VLAN is like having a "private channel" that directly connects only two providers, isolated from the traffic of the other IX participants.
TRUSTED BY

















// 10+ years consolidated experience
Our proprietary solutions allow end-to-end customization for any scenario.
Network / IP Backbone 20+ Tbps
Network connected to the main global hubs, ready for any challenge
Transparency & Telemetry
Track all traffic statistics & insights in real time
Patented solutions & ESG
In-house developed, patented and globally recognized solutions
24x7 trilingual support
24×7 trilingual support with escalation – talk to the CEO within 2 hours
99.995% SLA and SLO
We deliver the strictest SLA in the industry, with a very high NPS
Individual customization
Solutions implemented according to the traffic profile of each prefix.
FAQ
How is the service charged?
We offer affordable protection without taking advantage of those who are in an unfortunate situation; our charges are always based on the volume of traffic. We stress that nothing is charged until the incident is resolved.
IS IT POSSIBLE TO CUSTOMIZE MITIGATION RULES?
Perfectly. Our solutions offer great scope for customization, from thresholds to advanced payload inspection rules, challenge algorithms, ratelimit, etc.
Is it possible to follow something in real time?
Absolutely. All our solutions offer dashboards for monitoring traffic and attacks in real time, including forensic details and countermeasures applied to each anomalous event.
do i need to invest in any additional equipment?
Generally, no. In most cases, at least 95%, we are successful in implementing our clients’ pre-existing architecture, and there is no need to hire additional equipment or licenses.
Is there a minimum contract?
Yes, the minimum period is 12 months. In simple terms, our service works in a similar way to an insurance company, where the cost of mitigating DDoS attacks tends to fall according to the client’s profile and risk to the insurance company.
How is support provided? Is it provided 24x7?
Our support is provided 24x7x365 via WhatsApp, Helpdesk and telephone. Our team is always ready to respond to highly complex DDoS attacks, as well as scaling efficiently.
