O dia-a-dia dos provedores de acesso à Internet, em qualquer país, pode parecer tranquilo, mas não é. E no entanto, apesar de grandes dificuldades raramente percebidas pelos clientes que surfam na web, eles conseguem fornecer os meios para todos se conectarem à rede, em velocidade de banda larga e numa operação que raramente falha. Esse serviço também pode parecer bem simples. É apenas receber as solicitações de dados emitidas pelo dispositivo do cliente, transmiti-las aos servidores de destino e entregar ao cliente, como resposta, a informação solicitada. Mas essa tranquilidade pode parecer a mesma de uma lavoura de cereais vista de longe. Por causa da distância, ninguém vê insetos, fungos, vírus e outras pragas que ameaçam a plantação. Da mesma forma que também ninguém vê os malfeitores que fazem ataques de negação de serviço contra os provedores de acesso.
Embora esses ataques não sejam visíveis, eles são rapidamente perceptíveis. De um instante para o outro, os clientes não conseguem mais utilizar nenhum serviço da internet. A causa desse tipo de falha é que naquele intervalo de tempo todos os servidores do provedor de acesso estão sobrecarregados de solicitações sem sentido. Solicitações enviadas por dezenas e às vezes milhares de dispositivos organizados numa rede do mal chamada de botnet, às vezes criada pelo próprio malfeitor, às vezes alugada para ele para ser usada apenas por algumas horas, num ataque muito bem direcionado. Provavelmente, os provedores de internet estão mais vulneráveis a ataques DDoS, que podem afetar a estabilidade das redes e prejudicar a experiência dos usuários.
Existem ataques de negação de serviço o tempo todo
Existem na Internet sites que mostram em gráficos e tabelas, em tempo real, os fluxos de dados criados pelos ataques DDoS. Quem os conhece sabe que esses ataques acontecem o tempo todo. E na prática não há países imunes: todos os países do mundo são ao mesmo tempo origens e destinos. Alguns países tanto geram quanto recebem mais fluxos de dados do que outros, como é o caso da China, Estados Unidos, Rússia e até mesmo o Brasil. As razões para isso estão nas questões geopolíticas. Como, por exemplo, as guerras comerciais e, mais recentemente, conflitos bélicos.
Nesses sites da Internet, é possível visualizar um retrato bem nítido do risco que esses ataques oferecem aos provedores de internet. Nos últimos dez anos, segundo as estatísticas dos grandes provedores internacionais de serviços de rede, esses ataques se utilizaram de aproximadamente 60 diferentes estratégias para atingir suas vítimas. Cada estratégia é mais eficiente do que a anterior. Isso obriga os provedores de serviços de telecomunicações a adotarem mais proteções contra os ataques DDoS. Como alterar rotas, bloquear endereços de origem, mudar regras de firewalls, entre outras medidas.
Embora tenhamos referido genericamente os autores dos ataques como “malfeitores”, eles não se encaixam todos numa única categoria, pois são motivados por uma variedade de razões diferentes. Existem desde os ataques contra provedores de acesso para extorquir dinheiro até ataques de ciberativistas em nome de alguma causa que defendam. Já se prevê, por exemplo, que no mês que vem, Julho de 2024, organizações francesas serão bombardeadas com esse tipo de ataque apenas porque a França vai sediar os Jogos Olímpicos. Ataques tal como os que ocorreram no Brasil durante a Copa de 2014 e durante as Olimpíadas de 2016. Ciberativistas que não gostam da França ou dos franceses vão entrar em ação com ataques DDoS.
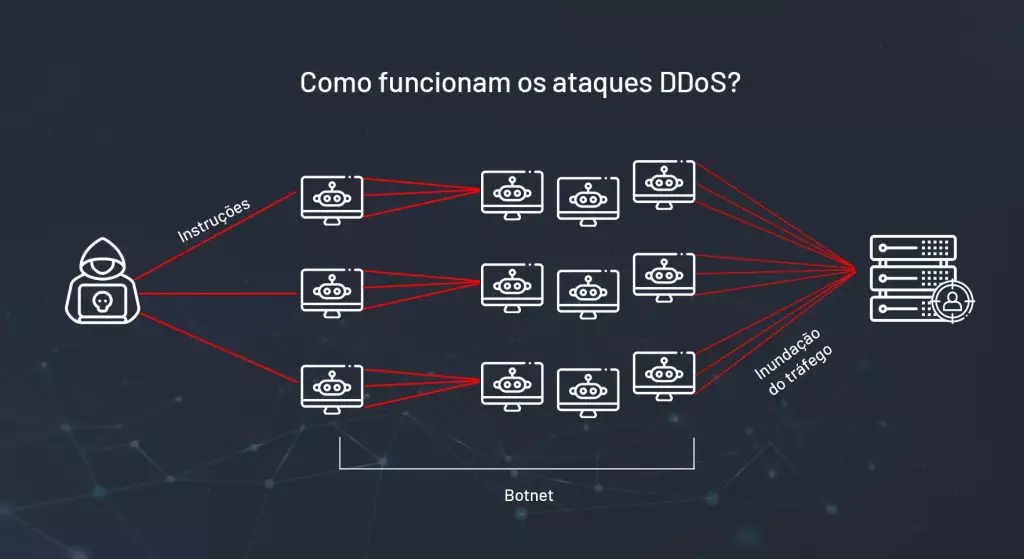
Contra os ataques DDoS, estratégias certeiras
Mas como os ataques de negação de serviço (DDoS) já existem há muito tempo, os provedores de serviços de telecomunicações e de rede os conhecem bastante bem e, por causa disso, têm várias maneiras de mitigá-los. Atualmente, as soluções baseadas em nuvem são recomendadas por eles como as mais eficientes, especialmente por causa da quantidade e elasticidade dos recursos disponíveis. Claro que qualquer empresa tem a opção de adquirir e administrar soluções locais, mas elas acabam sendo caras não só em termos de equipamentos, como em mão de obra. Já que é necessário ter especialistas que gerenciem todos os equipamentos o tempo todo.
Empresas especializadas nesse tipo de serviço, como é o caso da Huge Networks, investem em equipamentos de última geração. Além disso, dedicam recursos significativos à pesquisa e desenvolvimento de softwares específicos para o tratamento de tráfego malicioso. E como já existem ataques de grande volume, em algum momento eles poderão esgotar a capacidade local de mitigação instalada numa empresa. A partir desse ponto, a solução consistirá em desviar todo o tráfego para um “black hole”. Alcançando assim o objetivo do atacante – a empresa estará isolada da Internet, sem receber nenhum tráfego. Provedores de Internet, portanto, precisam estar sempre um passo à frente para mitigar ataques DDoS de forma eficaz.
Todos sabem: o barato sai caro
Num provedor de acesso, isso seria um desastre. Malfeitores têm atacado com frequência os pequenos e médios provedores de acesso à Internet do Brasil, pretendendo obter algum pagamento em dinheiro deles para suspender o ataque. Como esses atacantes sabem o valor dos serviços de mitigação, sempre pedem como “resgate” um total pouco inferior a isso, supondo que as vítimas preferirão pagar o resgate para economizar.
Felizmente, os provedores brasileiros têm se conscientizado de que o barato sai caro e cada vez mais estão buscado as soluções profissionais. Numa evolução estimulada por organizações como a Abrint, a Associação Brasileira de Provedores de Internet e Telecomunicações, que já agrega mais de dois mil provedores do país. E pelas empresas provedoras das soluções mais avançadas em segurança para as telecomunicações. Como a Huge Networks.
