Digital content is increasingly part of our daily lives, whether in the form of videos, audios, images or texts. They are accessed through different devices and platforms, making them essential for communication, entertainment, education and commerce. However, as the demand for online content increases, so do the challenges of protecting users from virtual threats, such as the DDoS attack. It is in this context that the protection of CDNs (Content Delivery Networks) has emerged as a solution for users when browsing the web.
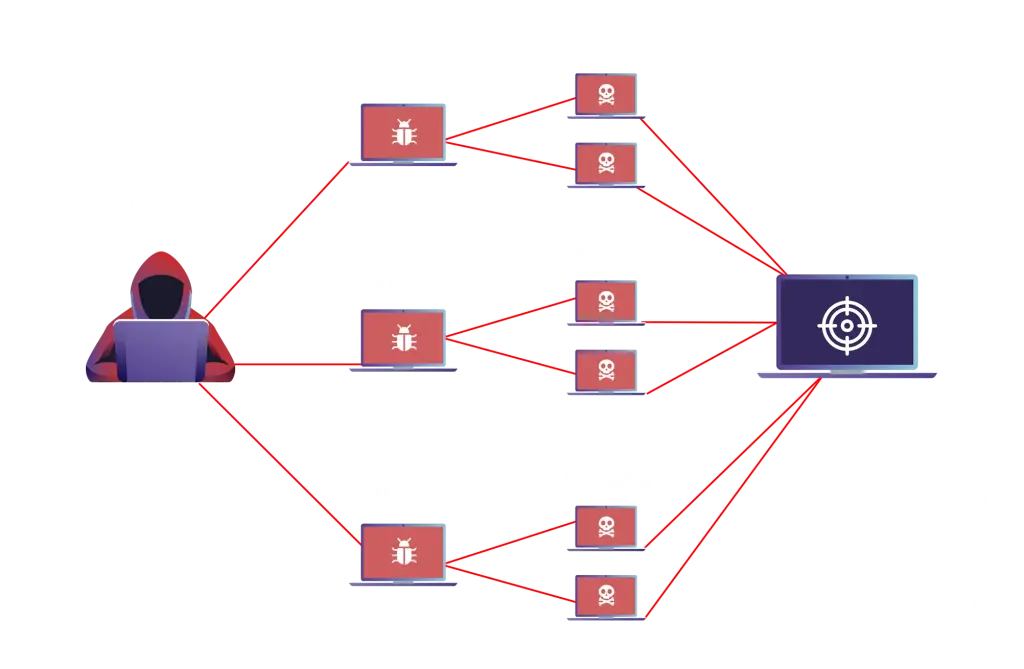
Infected devices in series
Every month, every year, the intensity of distributed denial-of-service (DDoS) attacks against Internet-connected devices is breaking records. One of the most recent, in February this year, reached 900.1 gigabits per second with 158.2 million packets per second. These figures have been rising since the first distributed attack was recorded. On July 22, 1999, a computer at the University of Minnesota in the United States was attacked by a network of 114 others that had been infected with the Trin00 script. As a result, mitigating the attack took two days.
Although such an attack can happen overnight, building the botnet takes time for the cybercriminal who controls it. In general, your starting point is the establishment of a “master” network node. This means that it infects a computer with software designed to spread and contaminate other devices. Such devices include:
- PCs;
- Routers;
- Cameras;
- Refrigerators;
- Among other things, anything that is connected to the web and can send data to an IP address.
The attack begins when the “master” sends a command to the contaminated devices, informing them of the address to be attacked and, if necessary, the time when the shots will end. In this way, the strategy used generally hides the true IP address of each attacking device.
However, DDoS brings not just one, but several risks to the scenario. There are many cases in the news where a denial of service attack has been used as a cover to hide intrusions into networks and systems. While the teams were busy solving one problem, another attack was underway.
It’s not uncommon to find similar reports, and you’ve probably heard them on the news or even suffered from this cybercrime.
DDoS is an asymmetric threat
In an article celebrating the 21st anniversary of DDoS, computer science professors Eric Osterweil and Angelos Stavrou, from George Mason University (Virginia, United States), and Lixia Zhang, from the University of California, outline a gloomy scenario, to say the least, for the evolution of these attacks. For the authors, “(…) it has always been easier to gain attack capability than defensive capability. DDoS is an asymmetric threat with an impedance mismatch between attackers and defenders. The gap between adversaries’ barriers to attack and the price to defend has always been large, but it is growing, and the status quo does not paint a pretty picture for the future: (…) we must discover the fundamental enablers of DDoS and we must use them to create effective defenses. We feel it’s time to re-examine the principles that underpin this problem space.”
The asymmetry to which the authors refer is present in at least three dimensions of the attacks. The first is the ease of gaining the capability. To give you an idea of this capacity, in 2010 there were 8 billion non-IoT devices and 800,000 IoT devices connected to the Internet, according to Statista. By 2023, the company forecasts that there will be 10.8 billion non-IoT devices and 19.8 billion connected IoT devices. In other words, there are a huge number of devices with weakened security available to be aggregated into attack networks (botnets).
And, to the surprise of many, CDN protection can be an ally in protecting any user, as we’ll see below.
Defense can be done in different layers
The second dimension mentioned by scholars is the cost of carrying out attacks: they are low for attackers and high for defenders. The third asymmetry is in the order of the damage, which can be huge even if it originates from a small attack – e-commerce operations, Internet access provision, TV signal distribution and other operations can be extremely damaged in one of these incidents.
The defense can be made at different layers of the operation. One possibility is to deploy protection at the layer of your devices, keeping them all up to date. Another alternative is to filter the traffic coming from the Internet while still at the ISP. It is also possible to filter traffic directly at the target of the attack.
But the experience of professionals in the sector has shown that the first alternative is not very efficient. The security of the devices is neglected by the owners, who rarely update the software and don’t always change the credentials received from the manufacturer. To make matters worse, the prices of many of the devices are so low that they prevent the manufacturer from including advanced security features.
The second alternative would be to filter traffic at the ISP. As the packet header contains not only the destination address but also the source address, it would theoretically be possible for an ISP to filter packets. Although the logic of the solution is simple, it is computationally expensive and time-consuming, making latency issues worse. And since ISPs are not (in general) the targets of denial-of-service attacks, they have no advantage in solving this type of problem. The last solution is to filter the packets on the target, which is generally impossible due to lack of knowledge and resources.
The protection of CDNs
For this reason, Eric Osterweil and his colleagues believe that network technology needs improvements to correct the lack of balance and symmetry. Until that happens – if it ever does – there is no better protection than CDNs, content delivery networks.
With extensive packet filtering capabilities, they do precisely the protection work that ISPs could do – but generally don’t. In fact, this is a service that CDNs ended up doing out of pure vocation: although they appeared in the late 1990s to alleviate the bottlenecks of increased Internet traffic in accessing content of interest to users, it soon became obvious that the points of presence for delivering this content would have the power to perform other functions – with packet filtering in “scrubbing centers”, for example.
In fact, CDNs have evolved from simple PoPs (points of presence) based on cache servers to edge data centers capable of real-time data analysis and processing. Whether we like it or not, CDNs took the necessary steps towards a vigorous presence in edge computing a long time ago. It seems that this trend will represent the first line of defense against denial of service attacks, while at the same time offering great computing power for our daily lives. This is the future for content delivery networks.
Do you have a specialized CDN service? Get to know HugeCDNthe Huge Networks content distribution network! In addition to the traditional features, it has an integrated WAF, latency of less than 40ms and a global presence. It’s a new way of guaranteeing even more protection for cdns!
This content was produced by Huge Networks. Our company protects your corporate network, accelerates cloud applications, mitigates DDoS attacks and keeps cyber threats at bay. Subscribe to our newsletter and stay up to date with the latest news on security and digital infrastructure!
